If you failed at setting up a Fortinet VPN Tunnel and don’t have a subscription with Fortinet this post is for you!
After setting up my AD at home with Enterprise grand networking, I set up a remote site at the “in-laws” with the 2nd DC. With both sites having Fortigate firewalls, I setup a IPsec Tunnel (site to site) between the two.
The next step was suppose to be easier, “Remote Access” to the home lab domain. It wasn’t as easy as I thought, I almost called this post, “When Cookbooks have bad recipes!”
Fortinet even has a recipe for it: https://docs.fortinet.com/document/fortigate/6.0.0/cookbook/786021/configuring-the-ipsec-vpn.
Two things I missed because the instructions weren’t clear (at least for me):
1. ” Configuring the IPsec VPN, Step 6: Enter a Client Address Range for VPN users. The IP range you enter here prompts FortiOS to create a new firewall object for the VPN tunnel using the name of your tunnel followed by the _range suffix (in the example, IPsec-FCT_range).”
FortiOS provides these addresses dynamically. Put in a “new range” that doesn’t exist!
2. ” Configuring the IPsec VPN, Step 10, In the Peer ID field, enter a unique ID, such as dialup1.”
This is important if you have other tunnels. “FortiOS will get confused where the traffic is coming from and going to without the [Peer ID].” Here I gave it “RemoteAccess.”
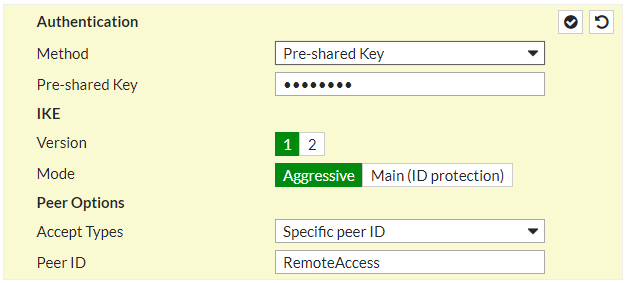
” Configuring FortiClient, Step 4: Expand Advanced Settings > Phase 1 and in the Local ID field, enter dialup1.” This same ID is needed on the Remote Clients configuration as such:
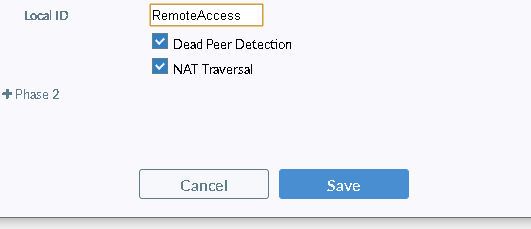
Hope this helps someone else.
